Delving into hot vs cold wallets crypto, this introduction immerses readers in a unique and compelling narrative, with a focus on security, accessibility, and best practices in managing cryptocurrency wallets.
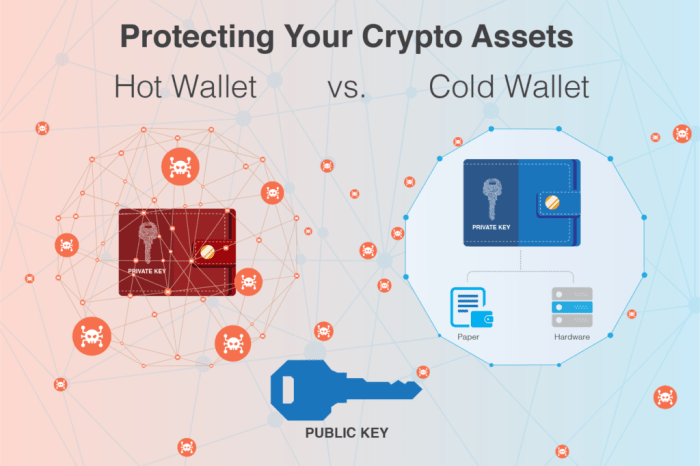
Hot wallets provide easy accessibility but come with security risks, while cold wallets prioritize security but may lack in convenience. By exploring the differences and best practices, readers can make informed decisions on safeguarding their crypto assets.
Overview of Hot and Cold Wallets in Crypto

When it comes to storing cryptocurrencies, users have the option of using either hot wallets or cold wallets. Each type of wallet has its own set of features and security measures.
When it comes to crypto trading, having the right indicators can make all the difference. Traders rely on various tools and metrics to make informed decisions, and knowing the best indicators for crypto trading is crucial. From moving averages to RSI, these indicators help traders analyze market trends and identify potential entry and exit points.
Hot Wallets, Hot vs cold wallets crypto
Hot wallets are connected to the internet and are more susceptible to hacking attempts. They are convenient for frequent trading and transactions due to their immediate accessibility.
Analyzing crypto trends is a key aspect of trading in the digital asset market. By studying price movements, volume patterns, and market sentiment, traders can gain a deeper understanding of the market dynamics. Tools like trend lines, support and resistance levels, and moving averages are commonly used for analyzing crypto trends and making informed trading decisions.
- Examples of popular hot wallets include Coinbase, Binance, and Blockchain.info.
- Hot wallets are ideal for storing small amounts of cryptocurrency for everyday use.
- They are often used by traders who need quick access to their funds.
Cold Wallets
Cold wallets, on the other hand, are offline storage solutions that are not connected to the internet. This makes them more secure against cyber attacks and hacking attempts.
Understanding crypto chart patterns is another essential skill for traders. Being able to interpret patterns like head and shoulders, triangles, and flags can provide valuable insights into market sentiment and potential price movements. By understanding crypto chart patterns , traders can improve their decision-making process and increase their chances of success.
- Popular cold wallet options include hardware wallets like Ledger Nano S, Trezor, and KeepKey.
- Cold wallets are best suited for long-term storage of large amounts of cryptocurrency.
- They offer enhanced security features such as private key storage offline.
Security Features Comparison: Hot Vs Cold Wallets Crypto
When it comes to securing your cryptocurrency assets, the choice between hot wallets and cold wallets plays a crucial role. Let’s compare the security features of these two types of wallets to understand their strengths and vulnerabilities.
Vulnerabilities of Hot Wallets
Hot wallets, which are connected to the internet, are more susceptible to hacking and cyber attacks compared to cold wallets. The constant online presence of hot wallets exposes them to potential security breaches, making them a prime target for malicious actors. Hackers can exploit vulnerabilities in the system or conduct phishing attacks to gain unauthorized access to the funds stored in hot wallets.
- Hot wallets are vulnerable to malware attacks that can compromise the security of the private keys used to access the funds.
- Due to their online nature, hot wallets are at risk of being targeted by hackers seeking to steal users’ funds.
- Phishing attacks can trick users into revealing their private keys or other sensitive information, leading to unauthorized access to the wallet.
Enhanced Security Measures of Cold Wallets
Cold wallets, on the other hand, provide enhanced security measures by keeping the private keys offline and away from potential online threats. By storing the keys in hardware devices or paper wallets, cold wallets offer a higher level of protection against hacking attempts and unauthorized access. Since cold wallets are not connected to the internet, they are considered more secure for long-term storage of cryptocurrency assets.
- Cold wallets store private keys offline, reducing the risk of exposure to online threats and hacking attacks.
- Hardware wallets, a type of cold wallet, offer additional security features such as PIN protection and encryption to safeguard the private keys.
- Paper wallets provide an air-gapped storage solution, ensuring that the private keys are completely offline and immune to online attacks.
Accessibility and Convenience

When it comes to accessing and managing your cryptocurrency, the choice between hot and cold wallets can significantly impact your overall experience. Let’s explore the accessibility and convenience factors of using a hot wallet compared to the more secure cold wallet options.
Accessibility of Hot Wallets
Hot wallets are connected to the internet, making them easily accessible from any device with an internet connection. This means you can quickly check your balance, send or receive funds, and make transactions on the go. The user-friendly interfaces of hot wallets also contribute to their accessibility, allowing even beginners to navigate the platform with ease.
Contrast with Cold Wallets
In contrast, cold wallets are offline storage devices, such as hardware wallets or paper wallets, making them less accessible than hot wallets. Cold wallets are more secure because they are not vulnerable to online hacks or cyber attacks. However, the trade-off is that accessing your funds stored in a cold wallet can be more cumbersome and time-consuming compared to hot wallets.
Scenarios for Suitability
Hot wallets are ideal for users who require frequent access to their cryptocurrency for day-to-day transactions or trading activities. On the other hand, cold wallets are better suited for long-term storage of large amounts of cryptocurrency that you do not plan to access regularly. For example, if you are actively trading cryptocurrency and need to make quick transactions, a hot wallet would be more suitable. Conversely, if you are holding onto your cryptocurrency as a long-term investment, a cold wallet provides better security for your funds.
Best Practices for Wallet Management

When it comes to managing both hot and cold wallets for your cryptocurrency, there are several best practices to follow to ensure the security and accessibility of your funds.
Securing and Backing Up Hot Wallet Keys
- Use a strong, unique password for your hot wallet to prevent unauthorized access.
- Enable two-factor authentication for an extra layer of security.
- Regularly back up your hot wallet keys and store them in a secure, offline location.
- Avoid sharing your private keys with anyone and be cautious of phishing attempts.
- Consider using a hardware wallet for added security and peace of mind.
Safely Storing and Accessing Cold Wallet Keys
- Generate your cold wallet keys offline to minimize the risk of exposure to hackers.
- Store your cold wallet keys in a secure, offline location such as a safe deposit box or a hardware wallet.
- Consider using a multi-signature wallet for added security, requiring multiple keys to authorize transactions.
- Create a detailed plan for accessing your cold wallet keys in case of emergencies, ensuring you can retrieve them when needed.
- Regularly test your backup and recovery process to ensure you can access your funds when necessary.
In conclusion, understanding the nuances between hot and cold wallets is crucial in maintaining the security of your cryptocurrency investments. By implementing best practices and choosing the right wallet type based on your needs, you can navigate the crypto landscape with confidence and peace of mind.